
Comcast has begun serving Comcast ads to devices connected to one of its 3.5 million publicly accessible Wi-Fi hotspots across the US. Comcast's decision to inject data into websites raises security concerns and arguably cuts to the core of the ongoing net neutrality debate.
A Comcast spokesman told Ars the program began months ago. One facet of it is designed to alert consumers that they are connected to Comcast's Xfinity service. Other ads remind Web surfers to download Xfinity apps, Comcast spokesman Charlie Douglas told Ars in telephone interviews.
The advertisements may appear about every seven minutes or so, he said, and they last for just seconds before trailing away. Douglas said the advertising campaign only applies to Xfinity's publicly available Wi-Fi hot spots that dot the landscape. Comcast customers connected to their own Xfinity Wi-Fi routers when they're at home are not affected, he said.
"We think it's a courtesy, and it helps address some concerns that people might not be absolutely sure they're on a hotspot from Comcast," Douglas said.
The Comcast advertising campaign came to Ars' attention after Ryan Singel, the co-founder of startup Contextly, was reading Mediagazer at a café in the North Beach neighborhood of San Francisco on Labor Day.
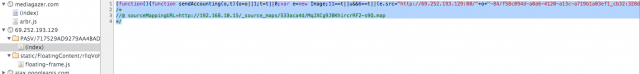
A small red advertisement saying "XFINITY WiFi Peppy" scooted across the bottom of the Mediagazer page and disappeared into the ether. It happened a few times, he said. Singel took screen shots of the advertisement loading and as it appeared on his screen. He captured some code, too.
"When a user requests to view a page, Comcast injects its JavaScript into the packets being returned by the real server," Singel said during an instant-message chat.

Unwanted injections
Security implications of the use of JavaScript can be debated endlessly, but it is capable of performing all manner of malicious actions, including controlling authentication cookies and redirecting where user data is submitted.
Comcast's Douglas says Comcast has nothing nefarious up its sleeve. What's more, Comcast has multiple layers of security "based on industry best practices" to keep out hackers wanting to exploit the Xfinity network, he said.
Seth Schoen, the senior staff technologist for the Electronic Frontier Foundation, reviewed the data pulled by Singel and said that "there ended up being JavaScript in the page that was not intended by the server."
Even if Comcast doesn't have any malicious intent, and even if hackers don't access the JavaScript, the interaction of the JavaScript with websites could "create" security vulnerabilities in websites, Schoen said. "Their code, or the interaction of code with other things, could potentially create new security vulnerabilities in sites that didn't have them," Schoen said in a telephone interview.
One way to prevent this from happening, he said, is for websites to encrypt and serve over HTTPS. But many sites do not do that.
Security expert Dan Kaminsky said in an e-mail that JavaScript injection has the potential to break "all sorts of stuff, in that you no longer know as a website developer precisely what code is running in browsers out there. You didn't send it, but your customers received it."
Net Neutrality Déjà vu
What Comcast is doing isn't without precedent. Airports have deployed so-called branded promotional hotspots, and there are plenty of companies that help businesses set up Wi-Fi hotspots that append ads via JavaScript injection. One of those companies is Front Porch, of Northern California, whose clients include Comcast, Cox, Time Warner, Bright House and Cablevision.But Comcast is one of the nation's leading ISPs, with more than 22 million customers nationwide. And there's no other major company that symbolizes the high-pitched fight over net neutrality, especially at a time when the Internet's future sits at a regulatory crossroads. That's because the Federal Communications Commission is taking public and industry comments through September 15 on whether it should adopt net neutrality and place broadband providers under the same law, known as Title II, that governs utilities like those delivering telephone service.
If the FCC decided to regulate broadband like a telephone utility, Comcast's JavaScript practice could come under scrutiny. And the policy question of whether broadband companies must deliver broadband without altering or initiating data packets could come front and center for a decision. "I think it shows why the FCC should have the authority under Title II to address this question," Marvin Ammori, an attorney and network neutrality activist and scholar, said in a telephone interview. "The FCC should be able to say, 'Hey Comcast, don't interfere with Internet connections by injecting these ads into Websites.'"
Many consumer advocates say that Title II regulation is needed to free the FCC or Congress to impose strong network neutrality rules that would force ISPs to treat all traffic equally, to not degrade competing services, or speed up Web services in exchange for payment. ISPs have argued that this would saddle them with too much regulation and would force them to spend less on network upgrades and be less innovative.
But there's a deeper, more nuanced point to be made on the topic, according to Robb Topolski, a network expert whose findings in 2007 helped launch the words "net neutrality" into the national consciousness. That year, Topolski concluded that Comcast was throttling BitTorrent by sending disconnect commands to customers engaged in peer-to-peer file sharing. A year later, the FCC ordered Comcast to stop the practice. A federal appeals court eventually reversed the FCC's decision because of a technicality, and the FCC is now mulling the idea of regulating broadband under Title II. A decision could come within months.
To Topolski, what Comcast is now doing is no different from before: Comcast is adding data into the broadband packet stream. In 2007, it was packets serving up disconnection commands. Today, Comcast is inserting JavaScript that is serving up advertisements, according to Topolski, who reviewed Singel's data.
"It's the duty of the service provider to pull packets without treating them or modifying them or injecting stuff or forging packets. None of that should be in the province of the service provider," he said. "Imagine every Web page with a Comcast bug in the lower righthand corner. It's the antithesis of what a service provider is supposed to do. We want Internet access, not another version of cable TV."
reader comments
195